Why e-TimeStamp Works
RFC 3161 timestamps are internationally-accepted, secure digital timestamps.
e-TimeStamps are SecureTime certificates
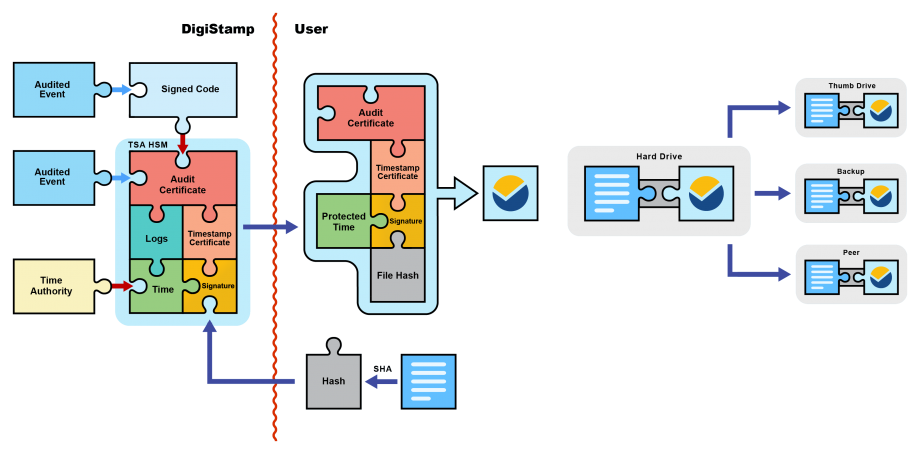
A DigiStamp e-TimeStamp is comprised of several components (as specified by the Internet Engineering Task Force's RFC 3161):
1. Unprotected information
a. The message digest: the cryptographic hash of your data
b. The time at which the timestamp was created: the SecureTime
2. A digital signature
a. A copy of the message digest and time that has been signed with the TSA's (Time Stamp Authority) current timestamp certificate
3. Certificates for verifying the digital signature
a. The public key of the TSA's audit certificate
b. The public key of the TSA's current timestamp certificate
PKI (Public Key Infrastructure) Digital Signatures
First we will discuss the digital signatures involved, because a timestamp is a digital signature. A digital signature is created when a signing key is applied to a message using an algorithm like RSA. In traditional, or symmetric, cryptography, the key used to encode a message would also be used to decode the message, much like a decoder ring from a cereal box. With the asymmetric crytography of PKI, we are now able to have a private key used for encoding a message and a separate public key for decoding a message. Instead of one ring that both encodes and decodes, now you need one ring for creating the message and another for reading it.
In this way, you can encrypt messages and then make them publicly available. Only individuals with the public key will be able to decrypt your messages, and holders of public keys will not be able to create new messages. Public key holders can also be certain that the message came from the private key holder, provided the key holder has been able to keep the private key protected. It for this reason we use FIPS-certified hardware, audited code, and generate certificates only after lock-down.
e-TimeStamp is an application of PKI digital signing for the purpose of creating a third-party witness, the Time Stamp Authority. A user sends our TSA a cryptographic hash of their data; it combines this with the current time and signs it using its current timestamp certificate. It then sends the digital signature back in the form of an RFC 3161 timestamp, attached to the public keys needed to decrypt it. By using the public key of the timestamp certificate, included in the timestamp, you can find the data's hash value and current time encrypted in the digital signature. Users can be sure the message came from our TSAthanks to the HSM (Hardware Security Module), and we take additional steps to ensure we maintain accurate, traceable time on our TSAs.
Cryptographic Hashes
But, let's take a step back. Digital signing may allow us to say this timestamp came from a TSA, but how does this cryptographic hash represent my data? I don't see my file in this timestamp. You don't see your files in your e-TimeStamps because they're simply not there. In fact, the only representation of them in our timestamps is a number.
SHA-1 of ("Your Data") = d42069f8f27556c5e91aa33a2d78fc0eff4895f3 = 1.2110288987633392239763068×10^48
Cryptographic hashes work because they are extremely specific and very difficult to reproduce. Their reproducibility can be tested by generating hashes of different versions of any file you choose. You will find that very small changes in your content make very large differences in the hash value. Most important, however, is the specificity of a hash value. The most accessible comparison we've come up with is the following:
The universe has existed for 13.7 billion years and the fastest thing in it is light. The greatest distance that could have been traversed is 13.7 billion light years. In order to rival the specificity of a SHA-1 hash, the weakest algorithm we support, one would need to pick out a point along that 13.7 billion light years with the precision of one femtometer. The width of a human hair, by the way, is 18 billion femtometers. A proton, a sub-atomic particle, has a width of 1.75 femtometers. Oh, and the SHA-1 was still 11,280,000 times as specific.
Cryptography's strength lies in the enormity of numbers imagined with no physical constraints. When you hash your data, you generate an essentially unique identifier. This identifier is added to the current time and digitally signed by the TSA within the protection of its Hardware Security Module. The certificate used to sign your timestamp was generated only after the auditing ceremony entombed the TSA in a certifiably locked-down HSM. The fingerprint of your data and the current signing key of our TSA are definitively bound together in our timestamp.