Strong Legal Evidence for Authenticating Your Data
Simply put, you need proof of what you've done and when you did it. Our service provides strong evidence for both.
In fact, we provide uniquely strong evidence.
No one can use our service to produce a false timestamp. Even we can't produce false timestamps. If someone offered us a million dollars, we still couldn't produce a false timestamp.
Why not? A DigiStamp timestamp offers you three layers of security:
- An audit trail from two independent authorities proving that our equipment does exactly what we say it does
- State-of-the-art software that meets the highest established standards
- Uniquely customized hardware that cannot be tampered with
Your data remains private in this process. Only the evidence, a SHA fingerprint, is transmitted to DigiStamp and we never see your actual document.
We use secure hardware that's uniquely certified.
Our software works within our IBM 4767 Coprocessor (an HSM), specially customized using an agreement with IBM to do nothing but generate our timestamps with absolute security. The coprocessor is FIPS 140-2 certified at level 4 of the rigorous National Institute of Standards and Technology (NIST).
Software-based solutions or solutions that do not have the clock secured inside the HSM leaves you vulnerable to charges of manipulating the proess. An adversary can always claim you paid the system administrator (even the administrator of an outside firm) to set the hardware or external clock to generate a false timestamp.
No one can set our systems to generate false timestamps
No one can hack our equipment, because our HSM has no external interfaces except the timestamp generator. There's simply no way in. Period. And any attempt to tamper with our equipment—even by us—stops it dead in its tracks. All old data is safe, but no new data can be created.
The Birth and Life of an Autonomous Robot
When we install, compile, and initialize our machines, we use two professional auditors. The independent Auditors hold multiple legal and professional certifications. These independent professionals witness the initialization, setting of the internal clock, and lock-down of the 4767 timestamping machine and provide durable evidence to present in any future legal proceedings..
The result of our multi-layered process provides you with stronger evidence than a notarized paper trail
Notaries can make mistakes, written signatures can be forged, paper trails can be modified after notarization. Our rigorous, fully-automated system provides solid, unalterable evidence of your files' integrity.
A DigiStamp timestamp provides a fully-automated chain of evidence.
-
There is an overview of how a timestamp is created and its content here.
-
Below are more details about the Audit Process.
DigiStamp Creates a Timestamp Robot
Machines can’t be tempted with money, and they don’t care whether they lose their jobs. The same can’t be said for programmers, system administrators, and bureaucrats, unfortunately.
That’s why we set ourselves the task of creating, in essence, a “timestamp robot,” a fully-automated process immune from human frailty.

hardware. The IBM 47xx Coprocessor is certified at levels 4 of the rigorous National Institute of Standards and Technology (NIST) using the Security Requirements for Cryptographic Modules
In 1999, under a custom development agreement with IBM, the 4758 was customized to eliminate all external interfaces except the timestamp function.
The HSM has its own unique keys for creating timestamps and auditing its own work. These are created automatically by the HSM when it’s installed, initialized, and witnessed by independent auditors.
The HSM has its own internal clock, which cannot be adjusted more than 120 seconds in any twenty-four hour period—and every adjustment is logged by the HSM.
When you send us a request for a timestamp, our system uses the 47xx, with its internal clock and keys, to create a timestamp—a unique “hash mark” signature—which it then sends to you. You store your original file and its timestamp as proof that the contents of your work existed at a point-in-time.
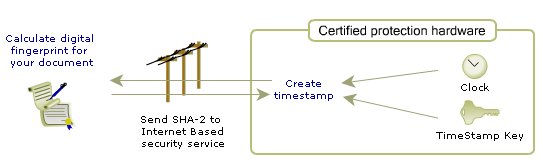
-
In The Electronic Signatures in Global and National Commerce Act (2000), federal law gives electronic signatures, contracts and records the same validity as their handwritten and hard copy counterparts.
-
In the United States, the Uniform Rules of Evidence Code ("UETA"), specify what makes electronic evidence admissible. The fundamental test is a process or system that produces an accurate result.
-
DigiStamp’s service meets this test. In fact, no one has ever even tried to challenge a DigiStamp timestamp. More details here
Inside the: Certified protection hardware
When we code, compile, and initialize one of our systems, two external auditors witness the “birth” ceremony and document the chain of evidence.
In an well defined process, the external auditors provide the evidence that the code we put into the 4767 HSM is of a known source and build, and that the 4767 card has had its external interface disabled, except the unique timestamp functions.
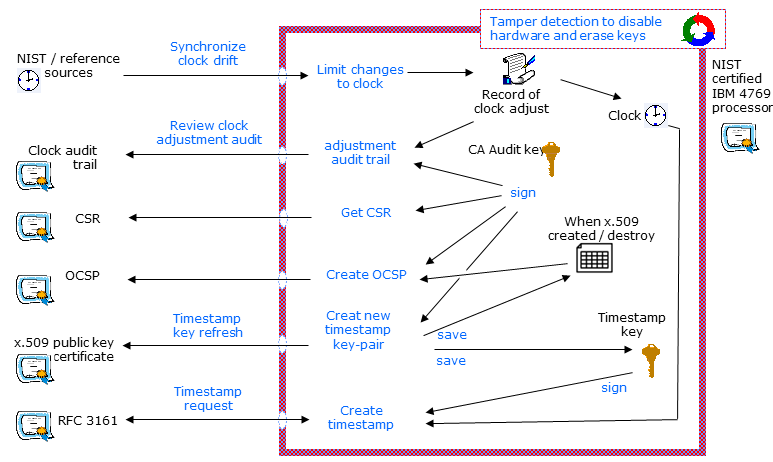
Security statements for the Audit ceremony:
-
The IBM 4767 Cryptographic Card is configured and initialized to a specific set of limited functions. Multiple parties witness and document the content of the software, the compilation and the initialization of the 4767 card.
-
An AUDIT key-pair is created inside the 4767. The private key portion of the AUDIT key-pair cannot ever be extracted from the tamper detecting hardware. The timestamp public key certificates are then signed by this AUDIT key to prove that timestamp key is reliably created and contained within this card.
-
The timestamp private key can be used only to create timestamps.
-
Private keys cannot be export/extracted from the 4767 hardware.
-
The clock in the 4767 hardware cannot be adjusted more than +/- 120 seconds in any 24-hour period. All adjustments are recorded and signed by an audit trail that is internal to the 4767.
-
No person can modify the card's security state without disabling the ability to create timestamps. Attempts to access the private keys or clock in 4767 hardware will reliably destroy the timestamp and AUDIT private keys.
When the system initializes, it creates an Audit key, which will henceforth sign and log everything that happens in the co-processor. No one and nothing can change or extract this Audit key.
The system will now accept only two kinds of inputs --- clock adjustments (all logged and signed by the Audit Key, automatically) and user requests for timestamps. Try to tamper, and the card stops. Its old work - your existing timestamps - are still valid, but it can’t do anything new.
How will you use this trusted third-party witness to your data?
DigiStamp has a full suite of options for corporations, developers, and small businesses. We offer a web-based service and on-site hardware options, an API Toolkit, SecureTime Proxy for no authentication and desktop software including a web application. Pricing available.
Learn more about how it works
