How a digital timestamp works
A trusted digital timestamp gives you strong legal evidence that the contents of your work existed at a point-in-time and have not changed since that time. The procedures maintain complete privacy of your documents themselves.
The result is simple, secure, independent and portable proof of electronic record integrity. By using digital signature technology and audited security our service provides an external witness (a timestamp signature) to the existence of your data, like an electronic or digital notary. We never see your actual data; it is that simple and here is how it works:
The trusted TimeStamp process consists of two parts:
|
|
| Try it Now! |
This method of creating a timestamp was published in public standards and laws; how to create a timestamp was not invented by DigiStamp. The digital timestamp was defined as part of the technology called Digital Signatures, or PKI (Public Key Insfrastructure). DigiStamp uses this accepted method and then adds an external audit and certified hardware to create a web-based security service that you can trust and afford.
Wikipedia provides a definition of digital timestamps here.
A fingerprint of your computer file is determined by our free software
When you timestamp a file, your computer creates a unique identifier, or fingerprint, for the file (a SHA Hash). The fingerprint is a unique number calculated from the file's contents. Mathematicians call this a hash function. If the file's contents were to change by even one character, a different number would be calculated. This accepted technique provides a design whereby it is computationally infeasible to find two different messages which produce the same number. Your data remains private in this process: Only the evidence (a document fingerprint) is transmitted to DigiStamp, and we never see your actual document. None of the content of your data can be determined from the fingerprint, so reverse engineering of the fingerprint into the document is not possible. Read more about the SHA hash at wikipedia or the "U.S. Federal Information Processing Standard" here.
The Internet links you to DigiStamp for the timestamp
DigiStamp is a TimeStamp Authority (TSA). By using the Internet, you electronically send the file's fingerprint to the DigiStamp computer. At the DigiStamp computer, we put the file's fingerprint and the current time into an envelope and add our digital signature. The result is a digital timestamp certificate that is returned and stored in your computer software. The process is safe; your file is never sent across the Internet, only the file's smaller fingerprint.
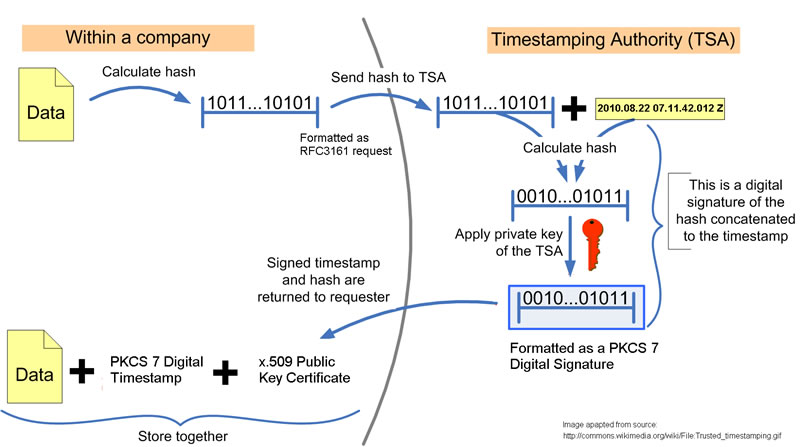
Your certificates are stored on your computer for easy verification
We give you software to store and manage your timestamp certificates. Each certificate can be used later to verify that the contents of your file existed at a point-in-time. The content and the format of a digital timestamp are defined by common standards and therefore can be verifed using a variety of vendor's software.
The process is safe, your file is never sent across the Internet. The process is reliable, the timestamp certificate proves that your file and its contents existed at a point-in-time.
-
Would you like more details? A good place to start is our Frequently Asked Questions.
-
Create an account and select from our free software. 25 timestamps cost only $10.
-
Read about the security and trust of our digital timestamps.
-
Information on the international standards for a TimeStamp Authority (RFC3161) and the technology here.
How will you use this trusted third-party witness to your data?
DigiStamp has a full suite of options for corporations, developers, and small businesses. We offer a web-based service and on-site hardware options, an API Toolkit, SecureTime Proxy for no authentication and desktop software including a web application. Pricing available.Try it Free!
How will you use this trusted third-party witness to your data?DigiStamp has a full suite of options for corporations, developers, and small businesses. We offer a web-based service and on-site hardware options, an API Toolkit, SecureTime Proxy for no authentication and desktop software including a web application. Pricing available. |
|
