The SecureTime® System
We are DigiStamp, architects and maintainers of SecureTime, the system which provides trusted third-party witness to data as e-TimeStamps.
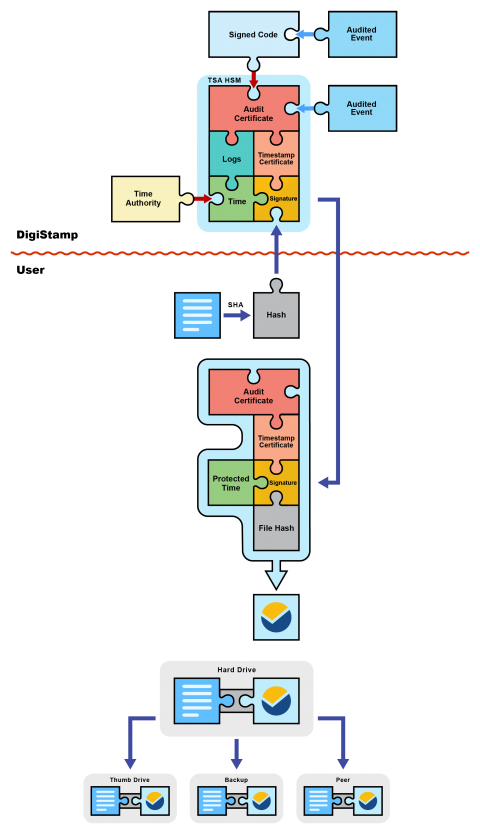
The SecureTime system was born when DigiStamp reviewed and compiled the source code for our Time Stamp Authority (TSA) Hardware Security Modules (HSMs) with the participation of two duly qualified auditors. The compiled code was immediately signed by all 3 parties and so has not been altered in any way since that event.
Later, the first TSA birth ceremony occurred. At this event DigiStamp loaded our signed software into an HSM built by IBM and certified FIPS 140 level 3 or higher. We then permanently closed all external management interfaces on the device under the watchful eyes of the two auditors. The first order of business for the newly created TSA was to create its audit certificate, which was promptly signed by the attending auditors. This audit certificate is used to sign all of the work the TSA will perform to manage its internal clock and create timestamp certificates.
Now, the TSA generates its first timestamp certificate and signs it using its own audit certificate. This timestamp certificate will be used to create e-TimeStamps. The TSA will use many different timestamp certificates in its life, each being securely destroyed before the generation of its successor. You can see the history of these timestamp certificates on our website.
In its life the TSA must be able to adjust its clock for drift in order to achieve the +/- 1 second accuracy of SecureTime. These adjustments are internally limited to a maximum of 50 seconds per 24 hours, or a little over 5 hours per year. All adjustments are logged and signed with the TSA's audit certificate. We use the consensus of multiple UTC sources provided by NIST and the USNO, and confirmation with EU-trusted sources, to keep our clocks accurate. There are signed logs linking the exact time in each e-TimeStamp to the birth ceremony, code signing event, and trusted time authority.
The TSA has been born and is now ready to create e-TimeStamps, the trusted digital timestamps.
The creation of an e-TimeStamp begins when a user selects a file for protection. The file's SHA hash (a digital fingerprint) is calculated with software on their computer and then transmitted to DigiStamp. We then provide this hash value to a SecureTime TSA which combines it with the current time, and some other information including a serial number, then signs the group with its current timestamp certificate. This newly created signature is the heart of the e-TimeStamp. The signature is passed back to DigiStamp; at this time we attach the public keys of the timestamp certificate and audit certificate in addition to plaintext copies of the protected time and file hash. All of this data is returned to you as an e-TimeStamp.
You are free to duplicate or distribute your protected file and its e-TimeStamp however you please. Each copy of the e-TimeStamp will include the information necessary to verify itself and tie it to the SecureTime system.