
Doctors and Accountants
Your work is trusted, are your records?
How much would it cost to defend yourself?
Records Integrity is Critical
If your work is ever wrongfully challenged, your records will be your best tool to vindicate yourself. e-TimeStamp trusted timestamps are a gold standard in demonstrating records-integrity thanks to rigorous implementation of international standards.
You can use us for CPA Audit Documentation (SAS 103).
We aid in compliance with HIPAA, SOX, and CFR 11.
Why use e-TimeStamp?
- Prove your data existed in its unaltered state, then and now
- Bind your name to your work to add evidence that its content originated with you
- Possess strong legal evidence backed by international standards
- Integrate our software into your existing software tools
- Provides a viable, low-cost solution to data integrity in electronic workflow
How it works
|
First, a digital fingerprint of your file is generated on your computer. |
See how easy it is to get protection! |
|
Next, this digital fingerprint is sent to a DigiStamp Timestamp Authority. |
The Timestamp Authority creates a timestamp with the fingerprint, the authority's digital signature, and the current time.
The timestamp is returned to you as a certificate, for your safe keeping, verifying the file's existence at the moment of timestamping. This certificate is proof that the file has not changed since being protected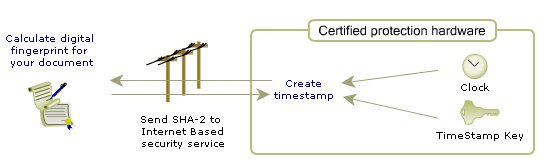
Important Considerations:
- You should include your name in the file that you timestamp, otherwise all that will be proven is that the file existed at a point-in-time.
- You must retain a copy of the file version you timestamped. A modified version will no longer have the same digital fingerprint so it will not be protected.
- You must retain a copy of the timestamp certificate to protect the authenticity of your records.
What you'll need to do
Protecting your records has never been this cheap or this easy:
First, you'll need to have a digital file of your records. If your records were not created digitally, this can be a scan, recording, or any other digital file that represents the work you need to protect.
Next, you'll need to make an account with DigiStamp. There is a minimum charge of $10 to use the service, but timestamps cost only $.40. Ten dollars allows you to protect 25 records.
Now, you're ready to make your first e-Timestamp with our web applications, or other programs like Adobe Acrobat or Microsoft Office.
Video demonstrations of how to use our web applications and the IP Protector are available.
Does an e-TimeStamp meet the legal standard for using electronic records as legal evidence?
Comply with HIPAA, SOX, and CFR-11
Has a timestamp been used to settle a legal dispute?
Why do I keep my own timestamps instead of DigiStamp?
How tamper-proof are the timestamps ?
What industry standards are supported?
More Questions and Answers can be found here.
An e-TimeStamp is a SecureTime certificate stating that a specific data file existed at a point-in-time. Every e-TimeStamp is created by an auditably locked-down FIPS-certified HSM. Independently verifiable evidence for $.40.
How will you use this trusted third-party witness to your data?
DigiStamp has a full suite of options for corporations, developers, and small businesses. We offer a web-based service and on-site hardware options, an API Toolkit, SecureTime Proxy for no authentication and desktop software including a web application. Pricing available.
Why you can trust it
DigiStamp provides strong legal evidence for authentication
Simply put, you need proof of what you've done and when you did it. Our service provides strong evidence for both.
In fact, we provide uniquely strong evidence, in part because we have implemented internationally standardized methods.
No one can use our service to produce a false timestamp. Even we can't produce false timestamps. If someone offered us a million dollars, we still couldn't produce a false timestamp.
Why not? A DigiStamp timestamp offers you three layers of security:
- An audit trail from two independent authorities proving that our equipment does exactly what we say it does.
- State-of-the-art software that meets the highest established standards.
- Uniquely customized hardware that cannot be tampered with.
Details on this security are available here.Details on why our product works are available here.
Our timestamps have not been successfully challenged in 10 years of operation. Many organizations have trusted us to protect intellectual property and records of great value to their operations.
